From Logs to Context: Evolving SIEM with Asset Intelligence
How to build intelligent detections through asset context and infrastructure intelligence
Security teams often face contextual challenges when analyzing logs at scale: understanding the broader environment where security events occur. While SIEMs can process massive volumes of data, raw logs provide limited insight into the state of systems, services, and infrastructure generating these events.
Consider a suspicious login alert. The raw event tells us a user authenticated from an unfamiliar location. However, critical questions remain: Was this a managed corporate device with hardware security keys? A compromised development instance in AWS? An unmanaged BYOD endpoint? Analysts spend valuable time gathering basic information without this context instead of investigating higher-priority threats.
This post explores how asset context improves analysis efficiency, enabling teams to make better decisions faster and build more precise detection logic. We'll examine practical approaches to enrichment, discuss data freshness challenges, and explore how this contextual layer enables more intelligent automated analysis.
The Asset Context Foundation
Modern security operations have evolved beyond traditional IoC-based analysis. As infrastructure becomes more dynamic and distributed, security teams need deeper context about the systems and services generating security events. This foundation of asset context helps analysts understand where to look, what to trust, and how to respond effectively.
Asset enrichment spans multiple layers across the technology stack, including identity providers. IdPs offer crucial insights about our organization and device trust. This includes vital security information such as hardware MFA settings, biometric authentication status, and OS versions. When investigating suspicious logins or privilege escalation, this context helps analysts quickly assess a device's trustworthiness and compliance with internal security policies.
Fleet management systems provide another vital layer of context around endpoint security. These platforms track detailed information about managed devices, including installed software, configurations, patch levels, and disk encryption status. Understanding whether a device is corporate-owned and properly managed helps analysts distinguish between acceptable deviations and genuine security concerns. For example, a developer logging in from a new location might trigger fewer alerts if we verify they use a fully managed corporate laptop with hardware security keys.
Cloud, container, and endpoint security platforms round out the asset context picture by providing deep visibility into the cloud infrastructure state. These tools track complex resource relationships, security group memberships, and compliance status across cloud providers. When investigating suspicious API calls or unusual network traffic, understanding the broader cloud context helps analysts assess potential blast radius and identify related systems that warrant investigation. Container security platforms add another dimension by tracking image vulnerabilities and runtime configurations, an essential context for modern cloud-native environments.
Implementing Asset Context
The effectiveness of asset context depends heavily on how and when we integrate this data with our security logs. Let's examine two real-world examples that demonstrate this enrichment in practice.
Consider a cloud security finding from Wiz identifying a critical vulnerability:
While this alert provides basic information about the vulnerability, enriching it with container and cloud asset context reveals the full security impact. We can see which workloads use this image, their exposure to the internet, and what sensitive data they process. We can also use identifiers such as externalId and region to query our logs for evidence of active exploits. This information is immediately available and expedites our alert assessment and judgment.
Similarly, endpoint security events become more actionable when enriched with device context from an IdP:
This context immediately tells us whether the device meets our security requirements and what additional logs we should examine. The presence of secure hardware also helps assess the trustworthiness of authentication events. If we see a login attempt from a new location but confirm it used WebAuthn with the device's TPM, we can be more confident it's the legitimate user rather than compromised credentials. Conversely, seeing password-only authentication from this device when we know it supports more potent methods warrants additional scrutiny.
Enrichment Pipeline
The timing and freshness of enrichment data significantly impact its utility. Teams typically choose between two enrichment approaches based on their specific needs:
Ingestion-time enrichment joins context data when initially processing security events. This approach works well for relatively static attributes like device ownership. It provides consistent historical context and performs efficiently at high volumes since the enrichment happens once during ingestion. However, it may miss recent changes to asset state or configuration.
Query-time enrichment fetches the latest context during analysis or alert generation. This method excels with rapidly changing attributes like compliance or resource status. While it can impact query performance, it ensures analysts always see the current asset state. This becomes particularly important when investigating time-sensitive incidents where recent configuration changes might be relevant.
Many teams implement a hybrid approach, enriching stable attributes at ingestion while performing targeted lookups for dynamic data during analysis. For example, basic device information might be joined during log ingestion, while current vulnerability status is queried during alert triage.
Asset-Aware Detection Engineering
Detection engineering fundamentally changes when we have rich asset context available. Rather than writing rules based on pure behavioral patterns, we can craft precise detections that understand the relationships between infrastructure changes and subsequent suspicious activity.
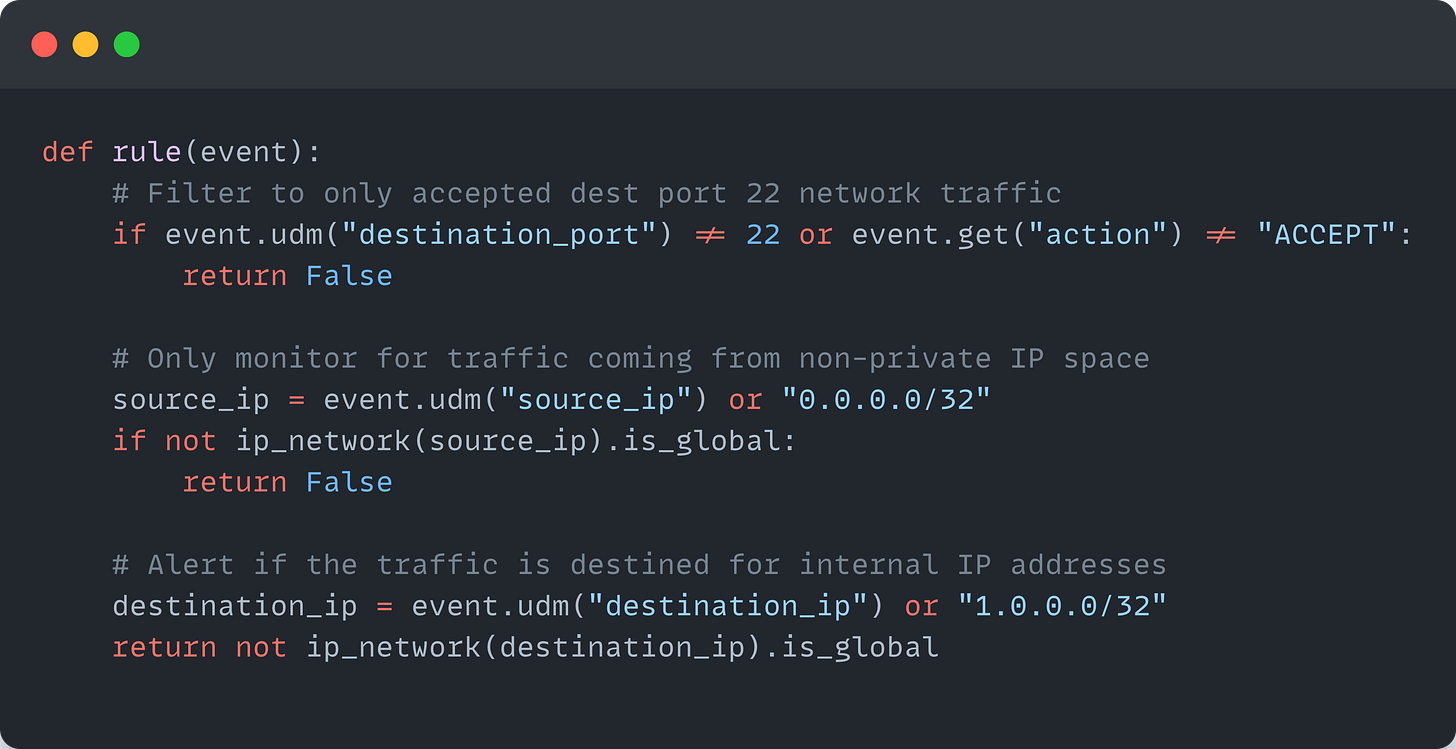
Let's examine a real-world example: detecting when a cloud asset becomes exposed to SSH access and is subsequently accessed from the internet. This scenario requires understanding both security posture changes and network activity:
First, we monitor for assets that become exposed to SSH:
Then, we watch for actual SSH access from the internet:
The power comes from correlating these events through asset identifiers. Here's how we tie them together:
This correlation creates a high-fidelity detection that understands the security posture change (SSH exposure) and the subsequent exploitation attempt. By joining on asset identifiers, we can precisely track the sequence of events affecting a specific resource.
More actionable alerts tell a complete story: "Production instance i-1234 became exposed to SSH at 2:00 PM due to a security group change, followed by successful SSH access from an internet IP at 2:15 PM." This context helps analysts quickly understand both the attack path and potential impact.
For Detection at Scale readers interested in implementing the concepts we've discussed, Panther’s now supports a direct Wiz integration! This means security teams can:
Build correlation rules that combine cloud security posture data with real-time logs
Incorporate rich asset context like configurations, vulnerabilities, and compliance status in detection logic
Build sophisticated correlation sequences that understand both behavioral patterns and infrastructure context
The integration exemplifies how deeper context helps improve detection efficacy, resulting in more informed and actionable alerts.
The Future of Contextual Security Analysis
As AI agents become more integrated into security operations, rich asset context becomes even more crucial. These agents can process and correlate vast amounts of contextual data to drive more intelligent analysis and response.
Future security workflows will leverage AI to automatically:
Build dynamic asset relationship graphs to understand blast radius
Identify high-risk system configurations based on historical incidents
Predict potential attack paths through your infrastructure
Recommend preventive actions based on asset context and security posture
The key is teaching these systems to think like experienced security analysts - understanding not just what happened but also where and why it matters. This contextual intelligence transforms simple log analysis into sophisticated threat detection that considers the full security implications of each event.
While we're still in the early stages of this evolution, the foundation is clear: the future of security operations will be built on the combination of comprehensive asset context, intelligent automation, and human expertise. Security teams that invest in these capabilities today will be better positioned to defend against tomorrow's threats.








Great article, for agents build around context, SIEM is a very good use case.
Fantastic article. Thanks, Jack. I was reading about Data Detection and Response (DDR) recently as the effective and timely protection of data requires appropriate context as well. Could be a topic you tackle in the future.