The Agentic SOC: From Isolated Automation to Orchestrated Intelligence
Why the future of security isn't one super-agent but a coordinated ecosystem that amplifies human expertise.
The promise of AI agents transforming security operations has generated both excitement and skepticism, and rightfully so. We've seen countless "revolutionary" technologies fail to deliver on their ambitious promises. Yet something fundamentally different is happening with the convergence of large language models, specialized agents, and emerging communication protocols. Rather than betting everything on a single, omniscient AI system, the future points toward something more nuanced: a network of specialized Enterprise agents that mirror how human security teams actually operate.
This isn't about replacing your SOC with robots. It's about creating an intelligent layer that amplifies human capabilities through coordinated machine intelligence. Just as your security team includes specialists in cloud security, incident response, and compliance, the emerging "Agentic SOC" will deploy purpose-built agents for specific domains, all communicating through standardized protocols. The result? Security operations that can scale beyond linear human constraints while maintaining the nuanced judgment that only humans provide.
From Single Agents to Agent Networks
We explored the concept of AI agents in "The Agentic SIEM," where individual agents could transform specific workflows like alert triage and investigation. But focusing on single agents misses the bigger picture. Security operations require coordination across multiple tools, data sources, and decision points. No single agent, no matter how sophisticated, can handle the full complexity of modern Enterprise environments.
Consider how your team investigates a potential insider threat. The process might involve checking HR systems for employee status, reviewing access logs across multiple platforms, analyzing data movement patterns, and correlating all of this with past incidents. Each step requires different expertise and access permissions. Trying to build one agent that does everything creates the same problems we see with monolithic applications: they become unwieldy, hard to maintain, and brittle when requirements change.
The alternative approach mirrors successful security team structures. Instead of one generalist trying to do everything, you deploy specialists:
Detection Engineers who understand log patterns and write rules
Incident Responders who know investigation workflows
Compliance Analysts who track regulatory requirements
Threat Hunters who proactively search for anomalies
Now imagine AI agents filling these specialized roles with excellent memory, tireless consistency, and the ability to work at machine speed. The challenge becomes coordination. How do these agents share information? How do they hand off tasks? How do they escalate to humans when needed?
This is where the real transformation begins.
The Protocol Revolution: MCP and A2A
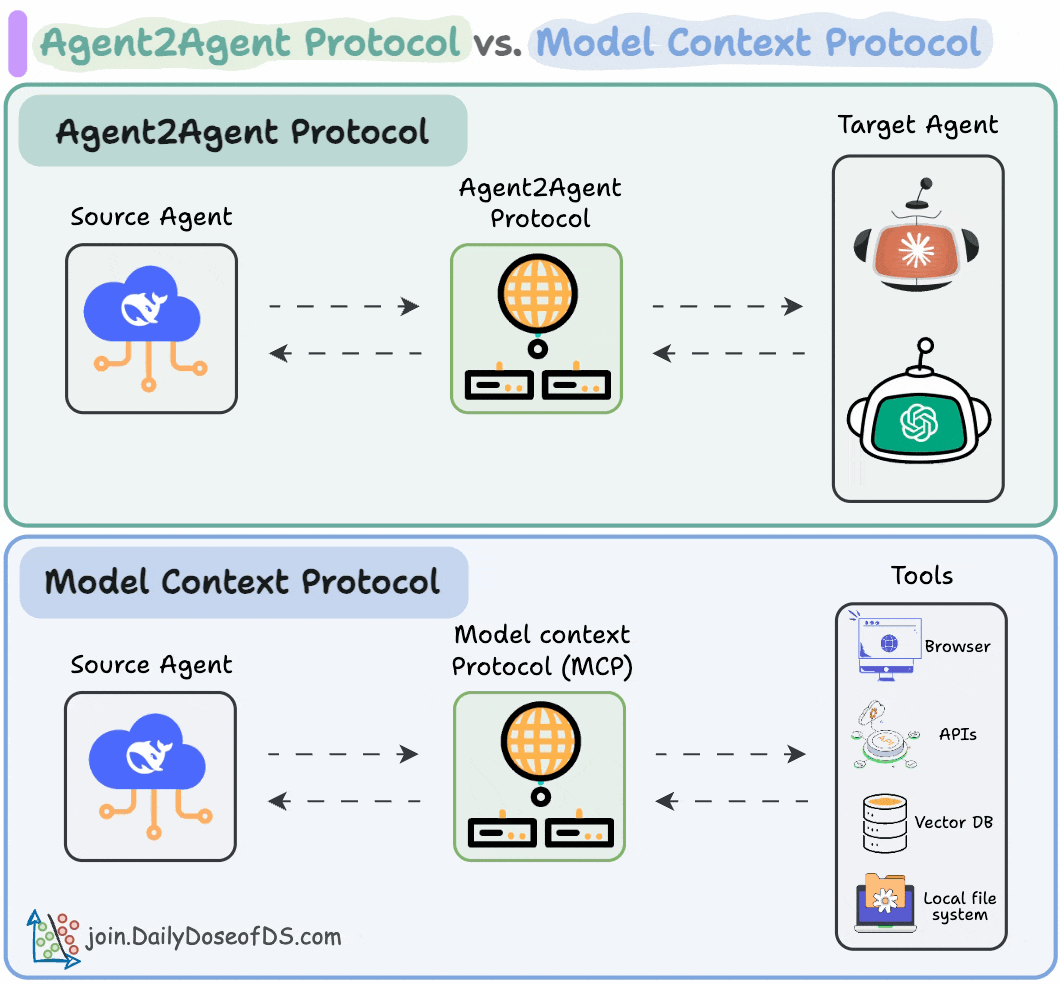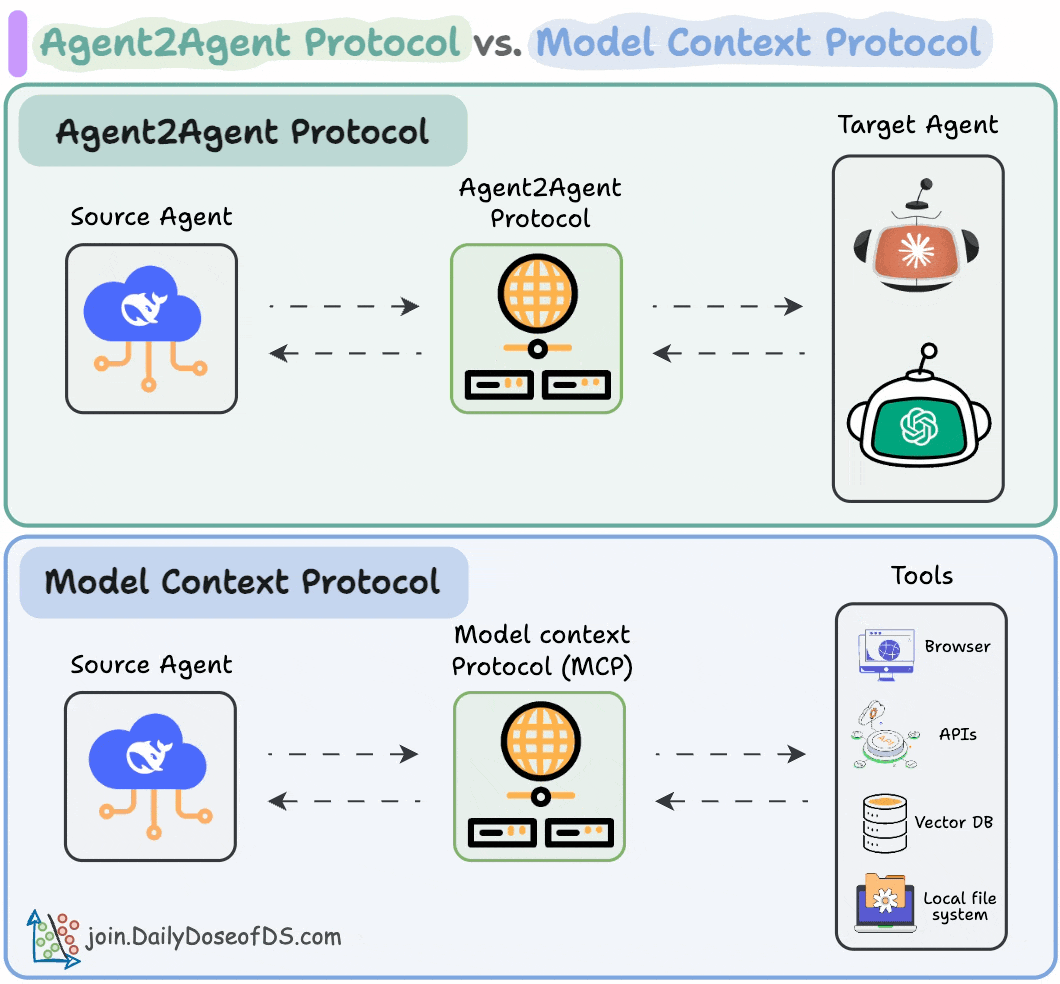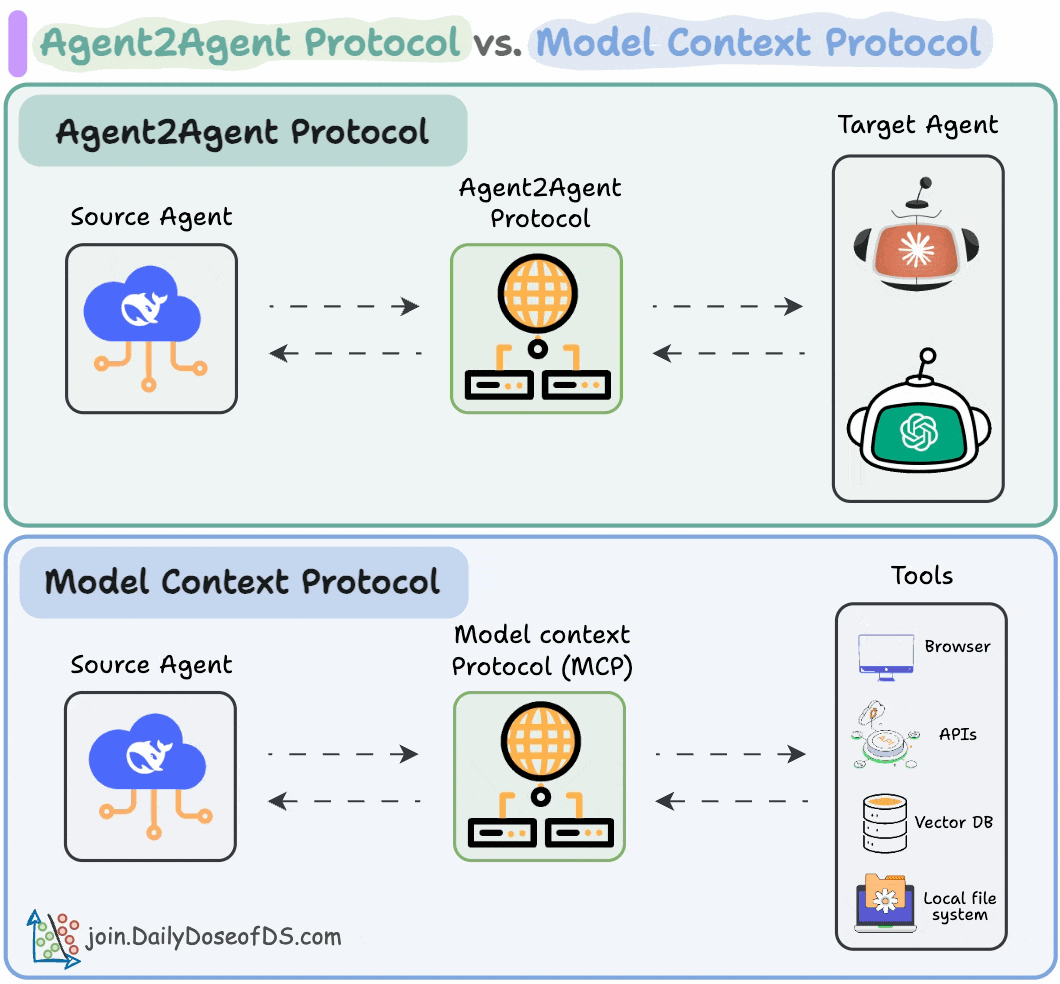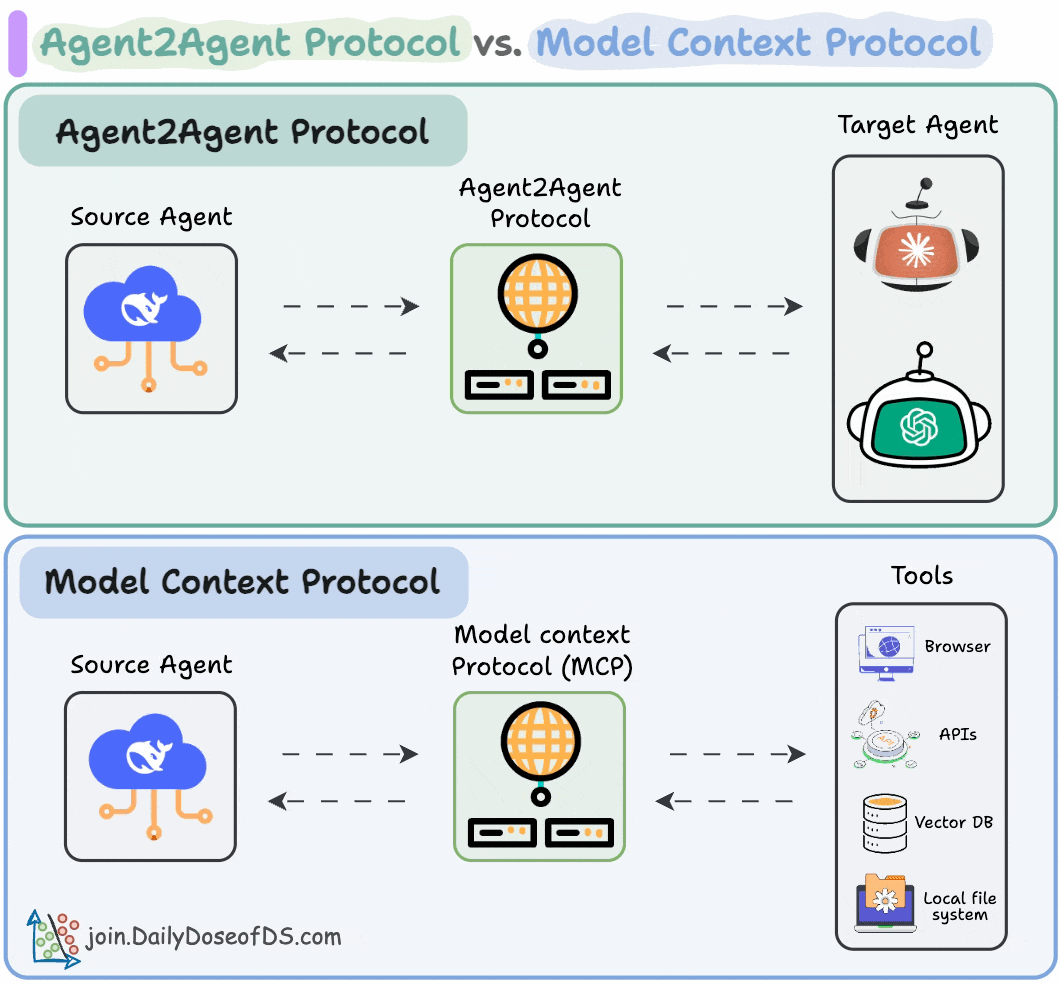
In our previous discussion of Model Context Protocol (MCP), we examined how this standard enables AI models to interact with enterprise tools through a common interface. But MCP represents just the beginning. The next evolution involves agents communicating directly with each other through emerging protocols like Agent-to-Agent (A2A).
Think of MCP as giving agents the ability to use tools, while A2A protocols give them the ability to collaborate. This distinction matters because effective security operations depend on both capabilities. An investigation agent needs to query your SIEM (via MCP), but it also needs to coordinate with your enrichment agent to gather additional context and your response agent to execute remediation actions.
The A2A protocol, recently released by Google, provides a standardized way for independent AI agents to:
Discover each other's capabilities through Agent Cards
Manage collaborative tasks with unique IDs and state tracking
Exchange information through structured messages and artifacts
Handle both synchronous and asynchronous communication patterns
These protocols solve a fundamental scaling problem. Without standardized communication, every agent integration becomes a custom project. You'd need to build specific interfaces between your detection agent and investigation agent, then different ones for your compliance agent, and so on. The complexity grows exponentially with each new agent you add. Sound familiar? It's the same N×M integration problem that MCP solves for tools, but applied to agent coordination.
Early A2A implementations show how agents can work together seamlessly. An investigation agent might send a task request to a forensics agent, which returns artifacts containing analyzed memory dumps. Meanwhile, a compliance agent monitors these interactions to ensure they follow data handling policies. All of this happens through standardized message formats and clear state management.
The combination of MCP for tool access and A2A for agent coordination creates the foundation for truly scalable agent deployments. But protocols alone don't create value. The real opportunity lies in how enterprises leverage these standards to build their own agent ecosystems.
Building Your Internal Agent Ecosystem
Here's where things get interesting for security teams. Instead of waiting for vendors to embed your specific business logic into their products, you can build lightweight agents that understand your unique environment and coordinate with any MCP-compatible tool or A2A-compatible agent.
Consider a practical example: your compliance requirements state that any access to customer data must be logged, reviewed by a manager within 24 hours, and retained for seven years. Today, you might have this logic scattered across runbooks, SIEM rules, and maybe some SOAR playbooks. Tomorrow, you could have a Compliance Coordinator agent that:
Monitors data access events from multiple sources via MCP
Communicates with Investigation agents via A2A to gather context
Routes appropriate notifications through your ticketing system
Ensures retention policies are followed across all systems
Generates audit reports that actually make sense to auditors
The key insight is that you build this institutional knowledge once, in your agent, rather than trying to configure it into every security tool you use. When you switch SIEM platforms or add new data sources, your agents adapt their MCP connections while preserving your business logic.
This approach scales beyond compliance. Imagine building:
An Incident Commander agent that coordinates response across multiple teams, automatically gathering context from various agents through A2A protocols and maintaining a real-time incident narrative. When an analyst says, "Investigate the Johnson account compromise," this agent orchestrates the entire workflow across your specialized agents.
A Threat Contextualizer agent that maintains knowledge about your specific environment: which systems are critical, what normal looks like for different teams, and how past incidents unfolded. Other agents query this one via A2A for context during their operations.
A Security Metrics agent that aggregates performance data from all other agents, identifying bottlenecks in your security operations and suggesting optimizations. It might notice that your detection agents are generating alerts faster than your investigation agents can process them, recommending specific tuning.
The building blocks exist today. The challenge is thoughtful implementation that enhances rather than complicates your security operations.
The Amplified Security Team
The implications for security teams are profound, but perhaps not in the way vendor marketing suggests. We're not heading toward fully automated SOCs with no human involvement. Instead, we're evolving toward a model where humans provide strategic direction while agents handle tactical execution at scale.
This shift fundamentally changes what security work looks like. Instead of analysts spending 80% of their time on data gathering and context switching, they focus on:
Strategy: Defining what agents should prioritize
Complex decisions: Handling novel situations requiring human judgment
Agent training: Teaching agents how to approach problem-solving
Quality control: Ensuring agent actions align with team expectations
The result is smaller teams achieving more sophisticated outcomes. A five-person team with a well-architected agent ecosystem might outperform a traditional 20-person SOC in detection coverage and response speed. This is about elevating human work to focus on problems that actually require human intelligence.
Success in this model requires new skills. Security professionals need to understand:
How to decompose security workflows into agent-suitable tasks
Prompt engineering to communicate effectively with AI systems
Agent architecture principles to build maintainable ecosystems
When to trust agent decisions versus requiring human review
These aren't replacements for traditional security skills. You still need to understand attack patterns, investigation techniques, and risk management. But you apply this knowledge differently, teaching it to agents rather than executing it manually.
The Context Window Revolution Is Already Here
We're no longer waiting for the future when it comes to context windows. Today's leading models already offer impressive capabilities:
Google Gemini 1.5 Pro handles up to 2 million tokens
Google Gemini 1.5 Flash processes 1 million tokens
Anthropic Claude 4 Sonnet manages 200k tokens
OpenAI's GPT-4o and o1 models support 128k-200k tokens
These massive context windows enable fundamentally different capabilities. Agents can identify subtle patterns across vastly longer time periods. They can maintain state across complex, multi-week investigations without losing details. They can understand the nuance of your environment without constant reminders.
But here's the critical part: you need to build your agent architecture today to leverage these capabilities. That means:
Designing modular agents that can expand their scope as models improve
Building robust state management that can scale with a growing context
Preparing your data infrastructure to feed these context-hungry models
The organizations that start building agent ecosystems now, leveraging current capabilities, will be positioned to take full advantage as models continue to improve. Those who wait may find themselves years behind.
The Path Forward
The Agentic SOC isn't arriving as a big bang transformation. It's emerging through incremental advances that compound over time. MCP enables tool integration. A2A protocols enable agent coordination. Massive context windows enable deeper analysis. Each piece builds on the others, creating possibilities we're just beginning to explore.
For security leaders, the question isn't whether to adopt agent technologies, but how to do so thoughtfully. Start small with focused use cases. Build expertise gradually. Learn what works in your environment before scaling up. Most importantly, maintain healthy skepticism while remaining open to genuine innovations.
The future of security operations will be shaped by how well we blend human expertise with agent capabilities. Organizations that find this balance, building agent ecosystems that amplify rather than replace human intelligence, will define the next era of cybersecurity. The Agentic SOC isn't just about technology. It's about evolving our entire approach to security operations for a world where the speed and scale of threats demand something more than human reflexes alone.
Check out our most popular posts below to continue reading about SOC + AI!
The Agentic SIEM
A practical guide to understand how AI agents will transform security operations from basic automation to intelligent analysis
MCP: Building Your SecOps AI Ecosystem
How the open Model Context Protocol creates new possibilities for connecting AI with enterprise security tools.